When you think of biometrics, you might think of something out of a spy movie, where the vault needs a fingerprint or eye scan to open, and wonder how realistic that really is. Or maybe you wonder about the privacy implications of using your face or fingerprint to authenticate to websites. These are all valid things to be curious about, especially since logging into websites with your face or fingerprint is so different from the passwords we use today.
The reality is that device native biometrics (like Apple’s Face ID, the Android fingerprint reader, or Windows Hello) are not some future sci-fi thing - you can use them to log into websites right now and they provide great security and privacy features. As this new technology starts to take the place of passwords, let’s clear up a few common misconceptions about this new form of authentication.
MISCONCEPTION #1: Your fingerprint or face data is not private and could be stolen and used to impersonate you.
One of the greatest advantages to using device-native biometrics for authentication is that none of your biometric information is ever sent to or stored by the website it’s being used on. That is a huge win for privacy and security.
When you log in to a website using your device biometrics, the website will generate a cryptographic challenge that is sent to your device. Your browser then interfaces with the fingerprint reader or face recognition components of your phone or laptop to sign the challenge. Passage verifies that the challenge is correctly signed before allowing you to log into a website. When your phone is prompting you for your face or fingerprint, you are unlocking the secure part of your phone that enables your device to sign the challenge - but none of that data is ever sent to any website, including Passage.
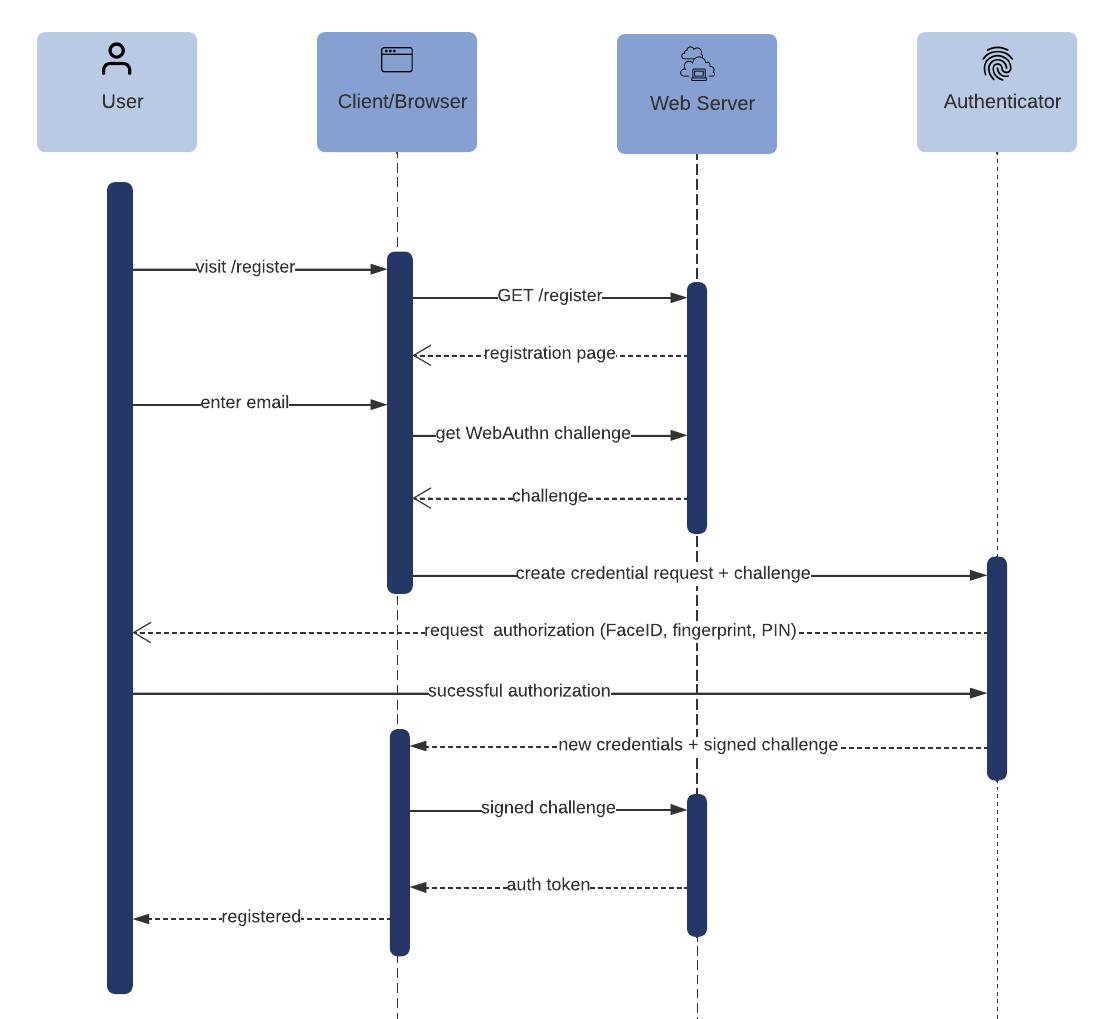
This is great for your privacy as a user, but it also has other security benefits. By not storing authentication materials on the website, there is no risk of big “password dump”-style breach. Passage does not hold hashes or anything else that can be used to log into your account. The only thing that can log in to your account is YOUR biometric on YOUR device. As a bonus, biometric credentials are scoped to a specific domain or website, which means that your credentials for example.com will never work for evil-example.com. This completely eliminates a common category of attack called phishing.
MISCONCEPTION #2: This isn’t any different than a password manager.
Password managers like LastPass or 1Password are a popular way for users to keep track of a large number of unique, complex passwords. These tools work by having a single password that unlocks access to passwords for each website. Mobile devices often have password managers built into them that leverage device biometrics. For example, on an iPhone, the Apple Keychain will save your passwords for all of the websites you visit and let you unlock those passwords using your Face or Touch ID.
Companies and developers cannot build those capabilities into their websites directly to get the user experience and security benefits for all of their users. Passage enables any web application to add a similar experience - one that provides the ease of Apple Keychain, for users across all platforms, without the need to worry about passwords and all the support needs that come with them (password recovery, account resets, etc.).
MISCONCEPTION #3: Face ID, Windows Hello, and other platform biometrics are only secure enough to be a second factor of authentication with a password.
Traditionally, devices have been used in tandem with passwords as a second factor of authentication. For example, you might receive a one-time code via text or use an authenticator app that is installed on your phone. While this form of MFA does improve security, it also adds an additional layer of difficulty to the end user experience.
With Passage, you can get the same number of login factors in a more efficient and user-friendly way. When you register for an account on a new website, you would enter your email, then be immediately prompted to register the platform biometric on your device. With just that one simple step, you are providing two factors of authentication:
- the ownership of the device you are on
- and your ability to authenticate your biometric on that device (via Face ID, etc)
If someone else has your device, they would still be unable to log into your account. Similarly, if they compelled you to present your biometric on a different device, it would also not work.
MISCONCEPTION #4: You won’t be able to log in on devices without a device’s biometrics.
This is a common critique of a device-based authentication method and it’s not wrong. The protocols that Face ID, Windows Hello, and other biometrics are built on are inherently tied to the device you are on. Passage is built to eliminate this issue by coordinating all of your different devices and providing you with the most secure login solution no matter where you are. Practically speaking, if your device has biometrics, Passage will prompt you to use it. If it does not, Passage will send a magic link to your email or phone number. You can click this link on any device and still be logged in on the original device you were trying to log in on. This allows you to always log in between different devices, while optimizing for the convenience and security of device biometrics.
At Passage, we believe device biometrics are the future of how we will authenticate on the internet. We are excited to share this amazing technology with the world and we believe that overcoming the misconceptions about the technology is an important step in moving the internet forward.
What other questions do you have about biometrics and passwordless authentication? Ask us in Discord.

